Cybersecurity researchers have found out a essential safety flaw in a man-made prudence (AI)-as-a-service supplier Replicate that will have allowed blackmail actors to achieve get entry to to proprietary AI fashions and delicate knowledge.
“Exploitation of this vulnerability would have allowed unauthorized access to the AI prompts and results of all Replicate’s platform customers,” cloud safety company Wiz said in a record printed this year.
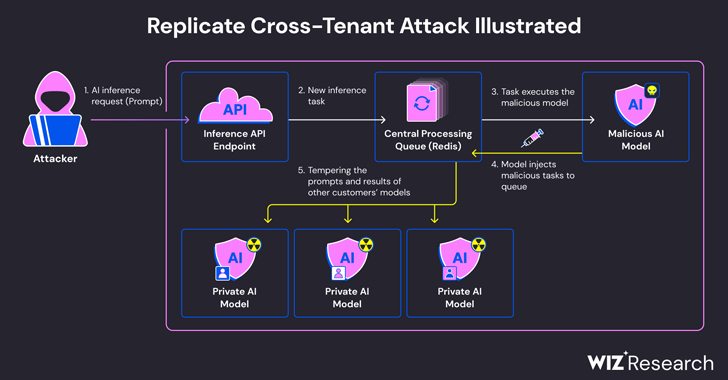
The problem stems from the truth that AI fashions are usually packaged in codecs that let arbitrary code execution, which an attacker may just weaponize to accomplish cross-tenant assaults by way of a unholy fashion.
Mirror makes usefulness of an open-source software referred to as Cog to containerize and bundle device studying fashions that would after be deployed both in a self-hosted condition or to Mirror.
Wiz stated that it created a rogue Cog container and uploaded it to Mirror, in the long run using it to succeed in far off code execution at the provider’s infrastructure with increased privileges.
“We suspect this code-execution technique is a pattern, where companies and organizations run AI models from untrusted sources, even though these models are code that could potentially be malicious,” safety researchers Shir Tamari and Sagi Tzadik stated.
The assault method devised by means of the corporate after leveraged an already-established TCP connection related to a Redis server example inside the Kubernetes mass hosted at the Google Cloud Platform to inject arbitrary instructions.
What’s extra, with the centralized Redis server being worn as a queue to top more than one buyer requests and their responses, it might be abused to facilitate cross-tenant assaults by means of tampering with the method to deliver to insert rogue duties that would have an effect on the result of alternative shoppers’ fashions.
Those rogue manipulations now not best threaten the integrity of the AI fashions, but in addition pose important dangers to the accuracy and reliability of AI-driven outputs.
“An attacker could have queried the private AI models of customers, potentially exposing proprietary knowledge or sensitive data involved in the model training process,” the researchers stated. “Moreover, intercepting activates will have uncovered delicate information, together with individually identifiable knowledge (PII).
The inability, which used to be responsibly disclosed in January 2024, has since been addressed by means of Mirror. There is not any proof that the vulnerability used to be exploited within the wild to compromise buyer information.
The disclosure comes a tiny over a pace upcoming Wiz detailed now-patched dangers in platforms like Hugging Face that would permit blackmail actors to escalate privileges, acquire cross-tenant get entry to to alternative shoppers’ fashions, or even break in the continual integration and steady deployment (CI/CD) pipelines.
“Malicious models represent a major risk to AI systems, especially for AI-as-a-service providers because attackers may leverage these models to perform cross-tenant attacks,” the researchers concluded.
“The potential impact is devastating, as attackers may be able to access the millions of private AI models and apps stored within AI-as-a-service providers.”